eSIM is the upfront SIM technology that is deemed to be adopted globally for long-range and mobile M2M/IoT applications. The fundamental feature of eSIM technology is remote SIM provisioning. A complete eSIM ecosystem is all about subscription management solution. At present, both proprietary and GSMA-compliant subscription management solutions are under development. The proprietary systems are developed by major device manufacturers and mobile network operators. Most of the proprietary solutions are incompatible with other eSIM solutions. As such, subscription solutions lack interoperability; they operate within closed and isolated environments.
GSMA-compliant solutions are developed in compliance with GSMA’s Embedded SIM Remote Provisioning Architecture. Supported by around 800 communication service providers all around the world, GSMA eSIM subscription solution is sure to facilitate global connectivity and full interoperability for M2M/IoT devices.
The GSMA-compliant subscription solutions are available as two separate variants according to the market segment they are developed for. There are two different eSIM solutions for Machine-to-Machine communication and consumer devices. The M2M segment includes industrial IoT devices like sensors, trackers, cellular modules, meters, and other industrial non-end-user devices. The M2M solution is based on GSMA’s M2M dedicated specifications – SGP.01, SGP.02, and SGP.11. The consumer segment includes consumer electronics devices like smartphones, wearables, laptops, and tablets. The consumer solution is based on GSMA’s consumer dedicated technical specifications – SGP.21, SGP.22, and SGP.23.
Both variants have different backend infrastructure platforms. The M2M solution has Subscription Manager – Data Preparation (SM-DP, which acts on behalf of Mobile Network Operator) and Subscription Manager – Secure Routing (SM-SR) as the backend infrastructure platforms. These platforms coordinate with the eUICC manufacturer, certificate issuer, and mobile network operator to provide remote SIM provisioning.
The consumer solution has a Subscription Manager – Data Preparation & Secure Routing (SM-DP+) and Subscription Manager – Discovery Service (SM-DS) as the backend infrastructure platforms. These backend platforms coordinate with eUICC manufacturer, certificate issuer, mobile network operator, and the end user to provide remote SIM provisioning where the Local Profile Assistant (LPA) may be integrated into the consumer device or the eUICC itself.
In both solutions, backend infrastructure platforms have different roles, and eSIM is configured differently to cater to the target solution. The M2M solution is server-driven and is based on Push-Model. This means that in the M2M solution, the eSIM profiles are managed by backend SM-DP/SM-SR servers for any subscription management operations. The consumer solution is client-driven and is based on Pull-Model. This means that Local Profile Assistant (LPA) integrated into the consumer device or the eUICC manages eSIM profiles for any subscription management operations.
eSIM Architecture for M2M solutions
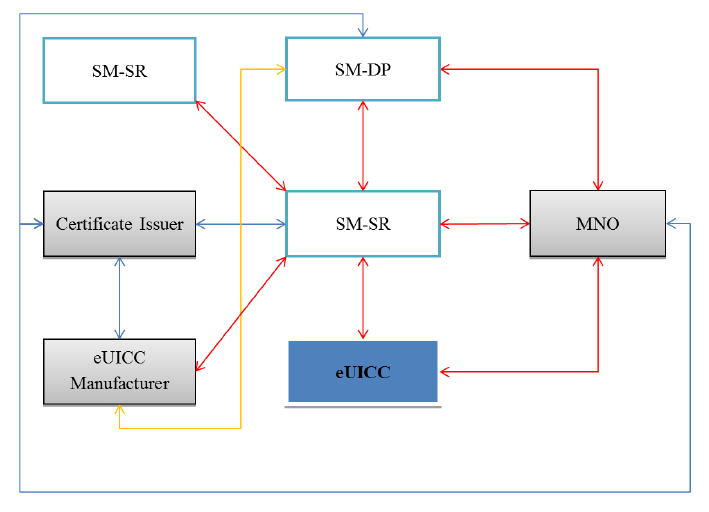
For M2M solutions, GSMA has specified remote SIM provisioning architecture, as illustrated in the diagram below.
Let us discuss different entities and their roles in this architecture
- eUICC manufacturer:- The eUICC manufacturer (EUM) provides the eUICC that contain a provisioning profile and/or one/more operational profiles. The eUICCs are delivered to the M2M device manufacturer. The eUICC manufacturer is responsible for the initial cryptographic configuration and security architecture of the eUICC. It is the eUICC manufacturer that has to provide services, tools, and documentation to SM-DP for creating an un-personalized profile for eUICC. EUM does not create an un-personalized profile on behalf of SM-DP. EUM is also responsible for forwarding platform management credentials associated with each eUICC to the SM-SR. EUM also needs to issue an eUICC certificate for eUICC authentication and certification to other entities, authenticated keyset establishment between eUICC and SM-DP, and authenticated keyset establishment between eUICC and SM-SR.
- Machine-to-Machine Device Manufacturer:- The M2M device manufacturer builds an M2M/IoT device, which is comprised of the eUICC and communication module. eUICC must have a default provisioning profile and/or operational profile that must be as per the agreement with respective Mobile Network Operator (MNO/CSP).
- Mobile Network Operator (MNO):- Mobile Network Operator (MNO/CSP) provides mobile network connectivity. It has to select at-least one SM-DP and have a direct interface to SM-SR. When the customer selects MNO, it initiates the download of a particular provisioning profile to the target eUICC. On the request of download, MNO checks and validates the certification and capabilities of the target eUICC. Once the download and installation of the provisioning/operational profile is complete, eUICC sends a confirmation to MNO, and MNO can manage the enabled profile on the target eUICC over the air (OTA). MNO can provide only limited service to the M2M/IoT device as per the respective provisioning profile.
- MNO Customer:- MNO customer is the contract partner with MNO for a subscription. It may not be the end-user. The customer uses an M2M device equipped with eUICC from the device manufacturer and the profile subscription from the MNO. It is the MNO customer that is responsible for the identification of the M2M device and the identification of eUICC.
- End-User: – End-user is the one who ultimately uses the M2M/IoT device and the services related to the enabled (eSIM) profile. End-user can be the MNO customer itself. Therefore, the end-user either directly relates to MNO or relates to an MNO customer.
- SM-DP: – SM-DP acts on behalf of MNO. It receives a profile description from MNO and creates an un-personalized provisioning profile for eUICC accordingly. For creating a profile for eUICC, SM-DP has to utilize tools provided by EUM. The tools and documentation exchanged between SM-DP and EUM are not standardized and may differ between different entities. SM-DP also builds personalized profiles for the target eUICC and generates personalization data (like network access credentials) based on data input from MNO. It is also responsible for installing a personalized profile on eSIM through SM-SR. The SM-DP must be at least GSMA SAS certified. SM-DP provides a secure and authenticated channel to eUICC to download and install profiles to ICC. On behalf of MNO, it is SM-DP that is responsible for managing profile enabling and deletion requests from eUICC through SM-SR.
- SM-SR:- SM-SR is responsible for establishing a secure and authenticated transport channel to the eUICC to manage the eUICC platform. SM-SR receives platform management credentials from EUM or previous SM-SR. Only one SM-SR can be associated with an eUICC at a point in time. However, SM-SR can be changed during the lifetime of the eSIM. It loads, enables, disables, and deletes Profiles on the eUICC according to MNO’s policy rules.
- Certificate Issuer – It is a trusted third-party that provides certificates for the EUM, SM-DP, SM-SR, and MNO. It is responsible for the authentication of entities (EUM, SM-DP-MNO, SM-SR) in the eSIM ecosystem.
- Initiator – Initiator can be any entity (EUM, SM-DP, SM-SR, MNO) that initiates a procedure (related to Remote SIM provisioning) in the eSIM ecosystem. It is an entity; it is authorized and authenticated by SM-SR at any time.
eSIM hardware and working
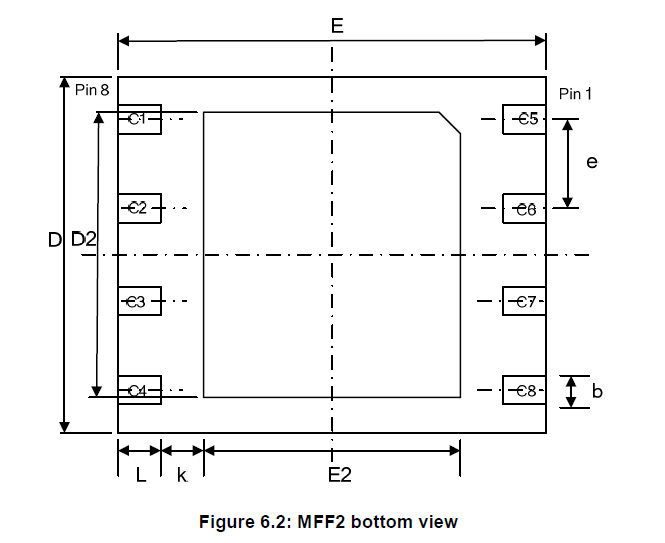
eSIM is basically a smart card based on GlobalPlatform Card Specifications (GPCS). It is manufactured as per standardized ETSI form factors (2FF, 3FF, 4FF, MFF2). It is loaded with a SIM operating system, and other software components like security domains and MNO enabled profiles. Within an M2M/IoT device, eSIM has a terminal interface that may be compliant with class A, class B, or class C operating conditions. In class A, eUICC has terminals (contact pins) for supply voltage (contact C1), reset (contact C2), a programming voltage (Contact C6), clock (Contact C3), and I/O (Contact C7). In class B and class C, eUICC has terminals (contact pins) for supply voltage (contact C1), reset (contact C2), clock (Contact C3), and I/O (Contact C7). For example, the following diagram show terminals of an eSIM in the MFF2 form factor.
The SIM exchanges commands with the IoT/M2M device controller to manage various subscription and services related functions. The commands can be associated with the implementation of various transmission protocols, management of application and file structure, and implementation of different security features. The structure of commands and responses is determined by the ETSI specifications (TS 102 221).
eSIM card architecture for M2M solutions
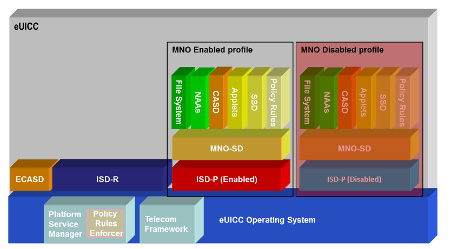
eSIM designed for M2M solutions have separate card architecture. By card, architecture refers to the software architecture of the eUICC smart card. The following diagram shows the eSIM card architecture for M2M solutions.
The eUICC is loaded with an eUICC operating system (SIM operating system) that supports all features defined in the GlobalPlatform Card Specifications (GPCS). As a SIM operating system, it includes a telecom framework, platform service manager, and policy rules enforcer. The OS is responsible for managing security domains, and MNO enabled Profiles (Provisioning/Operational profiles).
Security domains are on-card representatives of off-card entities that provide secure storage for cryptographic keys, security services for applications, a mechanism for loading applications, and access for off-card entities (SM-DP, SM-SR, MNO) using secure channel protocols. Security domains define properties that let security domain represent entities (SM-DP, SM-SR, MNO) for various roles in remote SIM provisioning architecture.
ECASD (eUICC Certificate Authority Security Domain) is created with eUICC at the time of its manufacture by EUM. It cannot be deleted or disabled after delivery to the M2M device manufacturer. This security domain contains non-modifiable eUICC private key, root public keys, associates certificates, and EUM keyset for key/certificate renewal. It is also required for the establishment of new keysets in the ISD-P(s) and ISD-R.
Issuer Security Domain – Root (ISD-R) is an on-card representative of SM-SR, and it is responsible for the execution of Platform Management commands. ISD-R is also created within eUICC at the time of manufacture and is associated with a default SM-SR. It cannot be deleted or disabled. It provides a secure OTA channel to SM-SR according to Platform Management Credentials (SCP80, SCP81 under GPCS). It also implements a key establishment protocol to change SM-SR.
MNO enabled profile that is responsible for subscription provisioning, and management includes ISD-P security domain, MNO-SD security domain, and various applications like file-system, NAA(s), CASD, SSD, Policy Rules and SIM Applets.
Issuer Security Domain – Profile (ISD-P) is the on-card representative of MNO or SM-DP delegated by the MNO. It is a separate and independent entity of eUICC. It contains a Profile that includes the file system, Network Access Applications (NAAs), and Policy Rules. This security domain consists of a state machine for creating, enabling, and disabling Profiles, keys for Profile management, key establishment protocol for personalization of ISD-P.
MNO-SD is an on-card representative of the MNO. It contains MNO OTA keys and provides a secure OTA channel with a mobile network operator (MNO/CSP). Once a provisioning profile from an MNO/CSP is installed on eUICC, ISD-P, and the Profile work in union.
eUICC contains two MNO profiles of which one is enabled while others remain disabled. Only one MNO Profile can operate and manage services at a time according to the contract and subscription with a communication service provider (MNO/CSP).
How eSIM works in M2M devices
eSIM/eUICC comes loaded with the SIM operating system, ECASD, and ISD-R at the time of manufacture from EUM. The eUICCs are delivered to IoT/M2M device manufacturers. IoT/M2M device manufacturer contracts with an MNO and loads a default MNO Profile to the eUICC. The profile can be changed anytime in the lifetime of eUICC by changing contract and subscription to a different MNO. When the IoT/M2M device is bootstrapped, it connects with default SM-DP/SM-SR servers and initiates subscribed services. Once the MNO Profile is downloaded and installed, it manages various services and applications accordingly. As M2M solutions are based on the Push Model, all management operations on eUICC are handled by the SM-DP and SM-SR servers.
While the SIM operating system contains all essential functionalities and services, IoT/M2M developers can design various SIM applets to enable different M2M-solution specific services and applications. These SIM apps (SIM applets) can be designed for value-added services like SIM health reporting, geofencing, quality of service reporting, mobile banking, TLS authentication, etc. SIM apps are based on Java Card, which is a subset of Java language. The SIM operating system itself is an applet written in Java Card.
Filed Under: Tech Articles


Questions related to this article?
👉Ask and discuss on EDAboard.com and Electro-Tech-Online.com forums.
Tell Us What You Think!!
You must be logged in to post a comment.