All of us understand the need of having an antivirus installed on our PC, but have you ever given thought about what are viruses? Why are they called virus?  Who created the first virus? Who makes virus and why do they make them? Can virus spread by opening a link or reading an email?
Who created the first virus? Who makes virus and why do they make them? Can virus spread by opening a link or reading an email?
 Who created the first virus? Who makes virus and why do they make them? Can virus spread by opening a link or reading an email?
Who created the first virus? Who makes virus and why do they make them? Can virus spread by opening a link or reading an email?If you are curious to know answers to these questions, let’s do some virus hunting…
WHAT IS VIRUS AND WHY ARE THEY CALLED SO?
In simpler terms VIRUS can be defined as a computer program (piece of code) which can spread across computers and network by making copies of itself, thus infecting the computer and usually it makes it copies without users knowledge.
But why are computer virus called virus; the reason is because of the striking resemblance to the real biological virus. The way they infect, the way they spread are a lot similar. A biological virus infects a person (host) which is its vehicle or carrier. The next task in hand is to reproduce itself, which it does by spreading to other cells (healthy) of the host. Then it tends to move from a person to other person and then repeat the whole process. This ensures the widespread of virus. 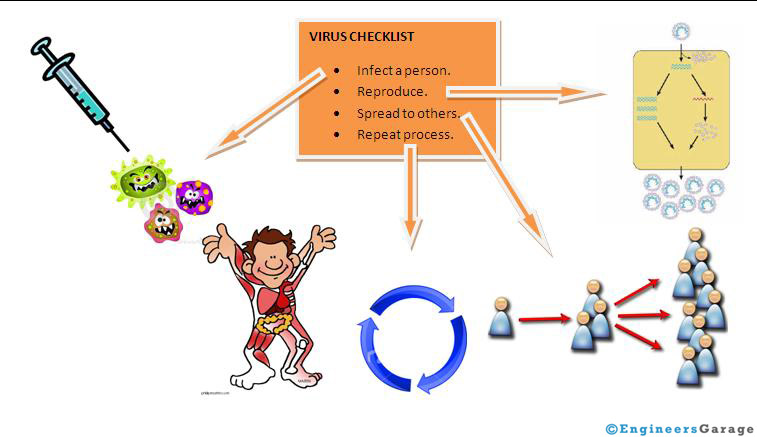

From this we can derive that how computer virus infects and how do they spread. In case of computer virus, the syringe is replaced by files, emails, and documents etc which are source of virus. The actual source-parent of virus is definitely a coder who writes the piece of code. They reproduce themselves by attaching with the files present in a PC and then tend to pass on to other PCs through internet, files etc. And this process continues. 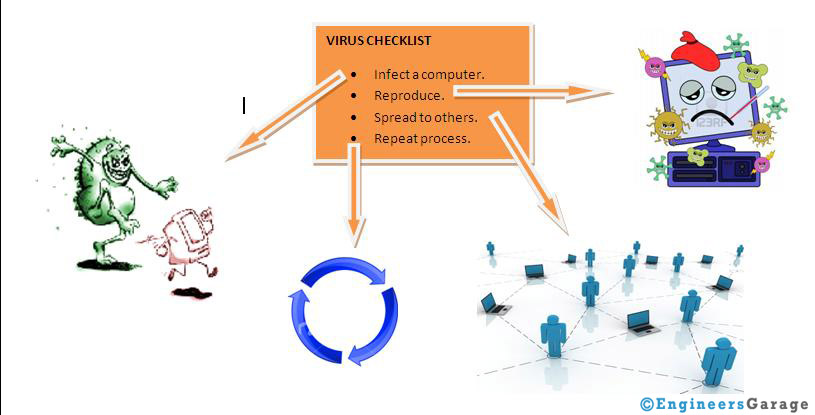

But they do differ from biological viruses in some aspects. Computer virus are manmade, and they are made to hinder the working, have fun which is generally not the case with biological viruses.
WHICH WAS THE FIRST VIRUS MADE AND WHY?
The first computer virus was developed by 2 Pakistani brothers in Lahore (Pakistan) in 1986. Its name was “Brain” and was developed to prevent the piracy of software made by them. The virus was not destructive in nature.
WHAT CAN VIRUS DO?
We know that viruses are programs only rather piece of code, so the task performed by them is defined by the coder. But still we can list the various tasks performed by virus as: 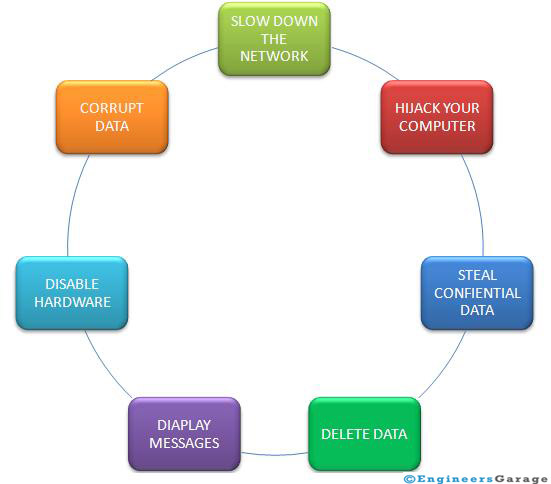

TYPES OF VIRUS
There is a long list of virus, but they can be broadly categorized into the following: 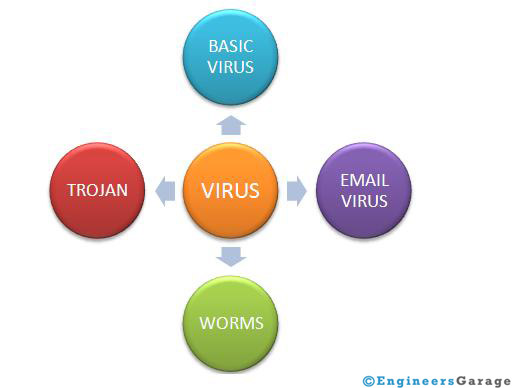

So let us look at the various types of virus.
· Resident virus
This type of virus lives in RAM (Random Access Memory) of the system. It makes it its home, so that’s why it is known as Resident Virus. One thing should be noted that everything that is executed in a system is via RAM (real memory of the system). So this virus infects and corrupts every file which is executed (open, closed, copied, edited, renamed etc.) in the system. 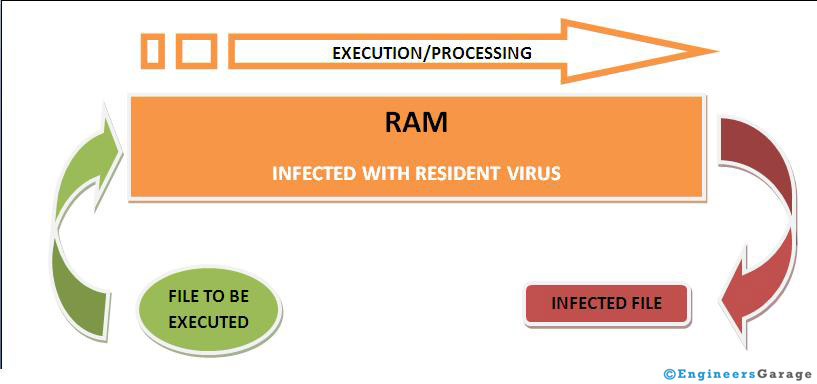

· Worms
Technically worm is said to be part of virus family, but worm is not a virus. It is said to be a part of virus family, because of its ability to reproduce and replicate itself and they are very good at it. FAST FACT Code RED worm replicated itself 2,50,000 times in nine hours. The main job of worm is to slow down the system or network (slowing the internet traffic).
· Trojan
They donot reproduce themselves or don’t infect files. Then what are they? They are ususlly in form of games (that is GAME = game + Trojan). So when ever a person clicks on it to install it and starts playing they start their job (task according to the code written by programmer). They generally tend to mess up with data by deleting the entire hard disk at time. They are also known as Trojan Horse.
· Boot Virus
These are one of the most dangerous viruses in terms of the damage they cause to the system. They infect the boot sector of the disk. The boot sector is the region which stores the information associated with disk (headers, inode, addresses etc.) and thus makes the booting procedure possible. If this virus infects the system then in most of the cases formatting the system is the only solution left.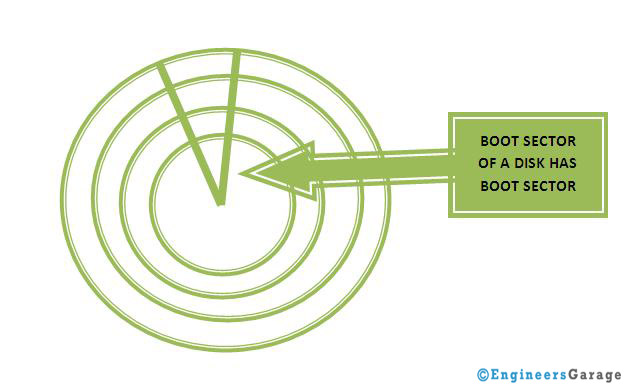
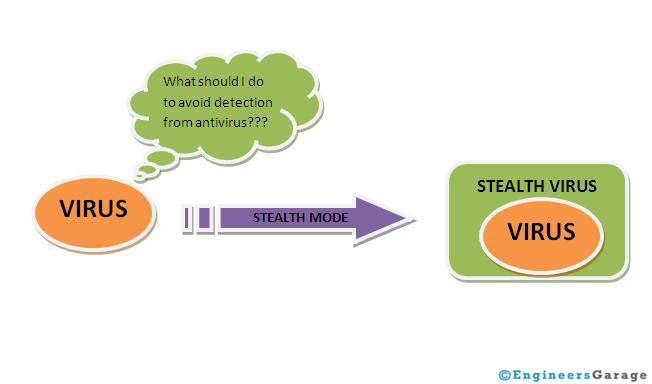
· Stealth Viruses
Stealth Viruses is some sort of viruses which try to trick anti-virus software by intercepting its requests to the operating system. It has ability to hide itself from some antivirus software programs. Therefore, some antivirus program cannot detect them.
· Directory Virus
These are the virus which spread very easily over the network. They change the path defining the location of a file/program or an application. So when a user executes an infected file then he/she basically gives a call to virus unknowingly which further infects the system. They tend to delete/move the original files in most of the cases.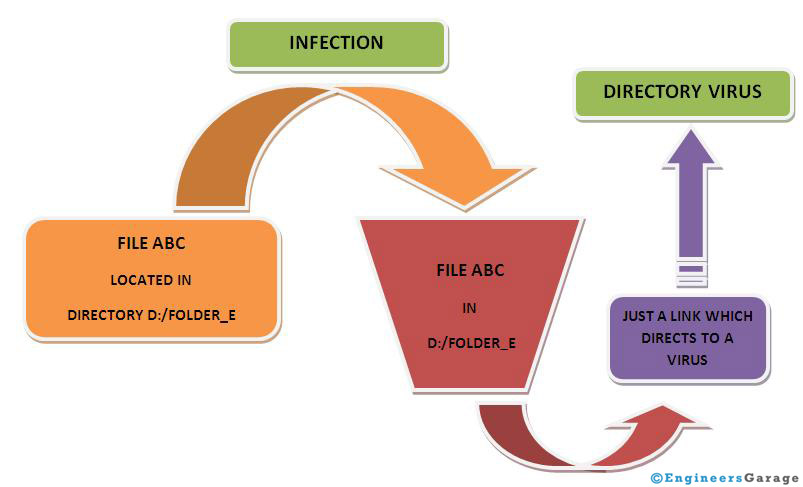
These are the virus which spread very easily over the network. They change the path defining the location of a file/program or an application. So when a user executes an infected file then he/she basically gives a call to virus unknowingly which further infects the system. They tend to delete/move the original files in most of the cases.

· Polymorphic Virus
They are the self evolving viruses. Every time they infect a new system they reinvent themselves and infects them in a new manner (they use different algorithms and encryption keys) thus making it tough for an antivirus to detect them.
They are the self evolving viruses. Every time they infect a new system they reinvent themselves and infects them in a new manner (they use different algorithms and encryption keys) thus making it tough for an antivirus to detect them.
· File Infectors
If you use internet then you would have encountered these viruses. Whenever one gets a pop up to download applications for free (free scanner, free antivirus, free wallpapers apps etc) then there is very high probability that user might be downloading an infected executable file (.exe or .com). So when a user executes these applications, he/she give a green signal to virus infected file to cause the damage to the system.
If you use internet then you would have encountered these viruses. Whenever one gets a pop up to download applications for free (free scanner, free antivirus, free wallpapers apps etc) then there is very high probability that user might be downloading an infected executable file (.exe or .com). So when a user executes these applications, he/she give a green signal to virus infected file to cause the damage to the system.
· Logic Bombs
As clear from its name, these viruses infects the system, corrupt the data if and only if certain conditions are met that is logic is met. They remain undetected until they become active, hence are difficult to be detected by antivirus.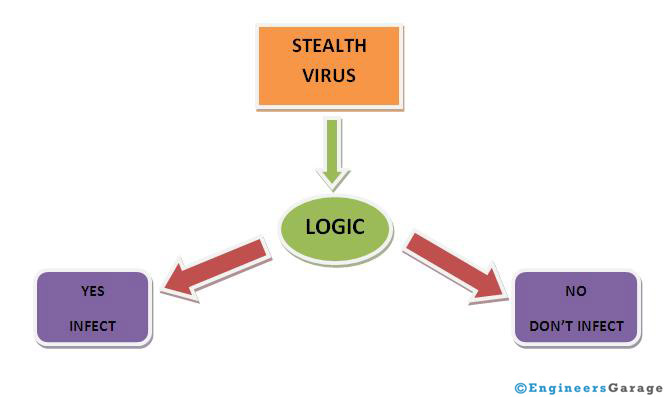
· Network Virus
As clear from its name, these viruses infects the system, corrupt the data if and only if certain conditions are met that is logic is met. They remain undetected until they become active, hence are difficult to be detected by antivirus.

· Network Virus
These kind of viruses spread over a network. It might be a local network (LAN- Local Network Area) or internet. They continuously search over a network searching for a flaw in systems security, and as soon as it gets a vulnerable system it infects it and repeats the cycle.
These were the most commonly found viruses. But there are many more types of viruses. They are listed below:
· Spacefiller (Cavity) Viruses
· Multipartite Viruses
· Direct Action Viruses
· Overwrite Viruses
· Macro Virus
· Encrypted Viruses
· Companion Viruses
· FAT Virus
· Nonresident Viruses
· Sparse Infectors
Protection & FAQs
FAQS???
· Can I get virus just by reading email?
Sorry but the answer is yes. Some virus, they infect the computer when a user reads an email. Basically the email contains a hidden message that is contains a script which is hidden, as soon as the person opens the email, the script runs and changes the system settings. Obviously antivirus these days disables the features of email having hidden script. Some examples are KAKWORM and BUBBLEBOY.
· Can I get virus just by visiting a website?
A website is basically web pages, which are written in HTML (Hyper Text Markup Language). Basically they cannot carry a virus, but still they can infect. They might call up a file or a program which is infected. They might be a mediator for spreading a virus, by directing you to a downloading link or having an attractive offer to allure a user into a trap.
· Virus over Bluetooth? Is it even possible?
Yes it is possible. Bluetooth devices enable themselves to locate each other and establish a link. This way they can transfer messages or data. It might send some personal message or data. The best way is to turn off “visible to other” features on the computer/phone or any other Bluetooth device.
PROTECTING YOUR COMPUTER
The best protection which one can have against virus is having antivirus installed on the system. Basically antivirus works against three things.
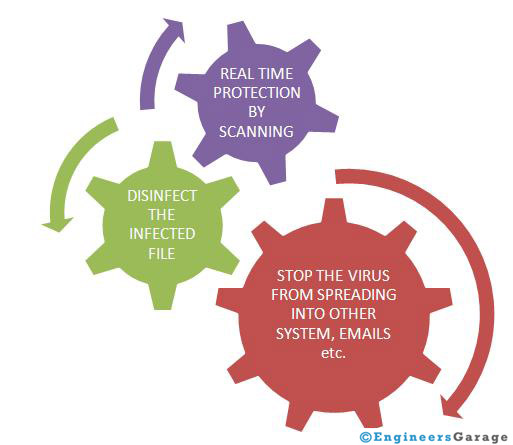
This is the first line of defense one can have against an antivirus. But at times this doesn’t assure that system will be protected from all kind of attacks. The person needs to be vigilant (because most of the times computers are affected to viruses because the user opens a file or program from a questionable unreliable source) and needs to regularly update the antivirus.
But there are few tips and tricks which one can follow in order to prevent infection:
· Most of the times virus infects a system through email attachments. So one should always be careful and avoid clicking on any email message from unknown source. Also spam mails should be avoided.
· One should avoid downloading from dangerous websites, because they allure a user by offering deals or by other means (avoid websites with adult content). So one should be careful.
· The operating system should be updated regularly. They download security patches which are essential for the systems protection. Even the drivers should be updated.
· If the system is a part of network, then it opens it to hackers, and whole load of viruses. So one should scan a file/program/game/folder before saving any on your personal system. And moreover file sharing should be disabled, and if it is necessary then only read permission should be given.
· If you are using internet then pop up blocker should be enabled. This feature is provided these days in the browser.
Rest all said and done, the user should be careful. Because it may seem to be a simple thing but the virus may ruin your work in a minute, or cause you embarrassment by making your personal life public.
So surf safe and be safe!!!
Filed Under: How to


Questions related to this article?
👉Ask and discuss on Electro-Tech-Online.com and EDAboard.com forums.
Tell Us What You Think!!
You must be logged in to post a comment.