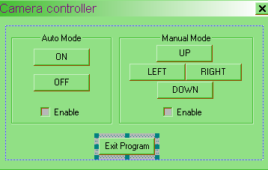
This is the most amazing and commercially viable project in which the web-cam attached to your computer will move in all four direction up-down and left-right with the help of your fingertips. The software written in VC++ will control two different AC motors with the help of computer mouse. The forward and reverse motion of…
Embedded Linux Tutorial & Basics
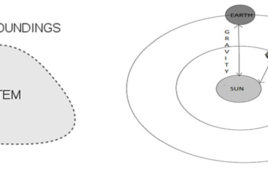
1.1) System A system is a set of different elements, which are interconnected inside a boundary, and may have abilities of input processing and output. Fig. 1: Image Illustrating System by Comparison to Solar System An example of system: Solar System itself is a good example of a system. Here the elements are…
Kernel Programming
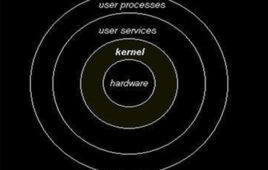
Kernel is nothing but the core of any operating system. It is the kernel that makes an OS entirely different from others. A kernel is actually a large block of code which keeps the system up and running from the time of booting, till shutdown. Kernel is that part of an OS which directly communicates with the hardware of the machine in which it runs and also with external hardware devices.The kernel can be viewed as resource managing code of an OS. It is responsible for managing and allocating resources like memory, processors etc. It also allows OS to communicate and control various external hardware devices like pendrive, memory card, keyboard etc.
Interfacing Serial Bluetooth Modem with Computer using ATmega16- (Part 41/46)
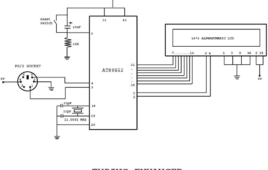
This project would give you a general idea about how to setup and interface any Bluetooth modem with your computer. There are many types of Bluetooth modems available in market, which vary in quality, cost, range, etc. Some of the well known Serial Bluetooth modems are AUBTM, BLUESMIRF, RN-41, HC-05 and HC-04.I would be using the last one i.e. the cheap Chinese Bluetooth module. It has limited functions and it can only work in slave mode. (Remember: Two slave modules cannot directly communicate to each other so be careful when you buy them.) The top range modules have a facility to work in both MASTER and SLAVE modes. It is Class 3 module so it range is very low. (Class 2 has a range of 10 meters and Class 1 has a range of 100 meters.)
Insight – How PS2 Connector Works
A gamer’s motion, a programmer’s voice, a DJ’s instrument and a designer’s brush; a single keyboard plays multiple roles in a computer. Similar is the case of a computer mouse that can make clicks to move a card in solitaire or open a web browser. For a computer buff of the current times, imagining a computer without these input accessories is impossible. Hence, it is utterly needed for these gadgets to tightly connect to the computer 24 x 7. Enabling a good connection are the PS2 connectors that have been in trend since a long time. Invented by IBM PCs, PS2 or personal station 2 connectors have reigned as sole connectors for keyboards and mouse for a long time. Easy manufacturing, ability to link tightly and fewer chances for connection error make it interesting to explore the insides of these connectors.
Typing Assistant based on 8051 microcontroller
Just as a PC software, that are being used in PCs to increase the typing skill and speed in a computer keyboard, this device has been developed to do the same job but without any PC. The device has a PS/2 keyboard port to connect a computer PS/2 keyboard (not an USB keyboard) and a LCD screen to display. When the circuit is assembled and programmed, a PS/2 keyboard has to be connected at the PS/2 socket provided in the device and it then serves as a portable TYPING ENHANCER. It needs only a 5V power supply and nothing else. It has no connection with PC.
CISC & RISC Architecture
Instruction Set Architecture(ISA) is important from user’s/ compilers perspective. Instruction Set Architecture is a ‘functional appearance to its immediate user/programmer’. ISA involves details like addressing modes, opcodes, registers, etc. Microarchitecture is important from the perspective of processor designer. Microarchitecture defines the logical structure or organisation that implements ISA. It involves details of pipelining stages, caches, physical registers, functional units, etc.Realization of hardware is important from the perspective of chip designer. Hardware is the actual “physical structure that embodies the implementation.” It involves micro-details of gates, transistors, wires, etc.Processors having identical ISA may be very different in organization. Processors with identical ISA and nearly identical organization are still not nearly identical.
Insight – How Laptop Cooling Pad works
With time and usage, many laptops face a common problem of overheating. It not only reduces efficiency of the laptop but can also cause damage to laptop peripherals such as hard disks or microprocessor. In order to assist laptop cooling fans, USB powered cooling pads have caught the fancy of computer enthusiasts and are widely in demand all over. Light weighted and economic, cooling pads boast of keeping the laptops temperatures within tolerable limits even during prolonged spells of extensive usage. Let’s have a look at a typical laptop cooling pad. The laptops are placed with the tilted side facing the user so that they can have easy access to keyboard. The laptop is held on the tilt structure through the rubber sponge pads that are placed at the edges of the cooling pad.Cooling pads are generally made of light weight plastic or aluminum mesh or a combination of both.
Insight – How Ethernet Cable works
If you ever connected a PC with a broadband connection you surely used an Ethernet cable to do it. Ethernet cables also called LAN cables or Cat 5 cables are often used in home networks. They are categorized into two types – Straight through and Crossover cables. Straight though cables are used to connect different types of devices (like PC to Hub) whereas Crossover cable is used to connect same type of devices such as PC to PC or Switch to Switch. Both the cables are almost identical except the wiring scheme of their end connectors. Depending on the type of the cable, straight through or crossover, both end connectors either have same or different types of wiring schemes, respectively. The connector consists of a mechanical lock which aids it to fix the cable in the port. Once a cable is thoroughly plugged into the device port a click sound is produced.
Joysticks
If you have ever visited a video game parlour to play a video game, you definitely would have used a JOYSTICK. Originally invented for flight controllers and motion simulators, they gained acceptance in number of systems, ranging from video games to industrial systems. Millions of video game enthusiasts, crane operators, etc. would owe a debt of gratitude to the inventor of this wonderful device, a joystick, though the inventor of this device is not quite known. The word ‘Joystick’ was used first by Robert Loraine and was cited in the Oxford English Dictionary, though he didn’t invent the device. Mr. Robert Esnault – Pelterie is also mentioned to be an originator of this buzz word. A E George along with Jobling used a stick for the first time when they flew an aircraft and this stick gained popularity as Joystick.
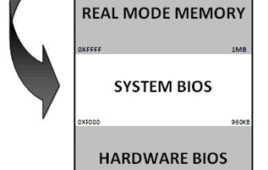
How Computer Boots Up?
How Computer Boots up? Have you ever given it a thought that when you press the power button on your laptop or PC, what happens behind the logo of Windows XP/Vista/Seven or Linux? From the pressing of the power button to the appearance of the login screen there are more than hundred components/peripherals that are…
Insight – How Computer ball mouse works
The first ever mouse was made by Douglas Engelbart of Stanford Research Center in 1963. It was one of the major inventions in computing world which supported keyboard to a large extent, making the experience of working on computer easier and faster. Since its invention different technologies have been developed to improve the efficiency of a mouse. A ball mouse is a type of electro mechanical device which uses a small ball as the key component to determine its movements and speed.The backside portion of the mouse shows the ball which is the heart of the ball mouse. When placed over a surface it rotates with the movement of the mouse. The ball mouse needs a flat surface with enough friction for smooth rotation of the ball and hence is generally accompanied with a mouse pad.
Introduction to LINUX
Twenty years ago, on August 25, 1991, a computer science student Linus Torvalds made a quaint announcement on the network that he’d been doing an operating system as a hobby for the 386(486) AT clones and now that he had good success in it, he would like to invite suggestions on what it should have and what not. Little did he know back then that he had just put the final piece of the big jigsaw puzzle called ‘Free Software Movement’ into its right place, Linux. By 1991, the world was witnessing an era of unprecedented hardware growth with more powerful computers being developed. The scenario was however poor on the software development front. By virtue of a highly successful marketing strategy, DOS reigned supreme and was the mainstay of almost every computer in all corners of the world.
Invention Story of Computer
Inventors have undoubtedly been heroes for all of us. By burning the midnight oil, they have gifted humankind with revolutionizing technology. Whether it is a mobile phone or a radio, they have never been miser in endowing the society with life transforming inventions. One such empowering invention has been of Computer. Not one but there are many geniuses behind the development and growth of this phenomenal technology. Wooden abacus laid basis for the computers long time back. By walking through annals of computer history, one can have a peek into rich legacy of 21st century’s technology. Back from 3000 B.C. abacus, which was a simple calculating tool introduced in China, is known to be the foundation of today’s computers.
Insight – How Computer Keyboard works
Computer keyboard is a device used to convert the keystrokes in to the electrical signals that a computer can understand. There are special types of switches and circuits to do this.When we press a key, it completes its corresponding circuit and an electrical signal goes to keyboard’s internal processor which detects the key which is pressed.A keyboard works on a 5V power which it takes from the computer through the Serial cable or USB. When we press a key on the keyboard, it pushes down the dome shaped rubber button which in turn electrically connects the top & bottom layer at that point and the signal is sent to the COB IC.
Insight – How Computer Optical Mouse works
The replacement of conventional ball mouse by the technically superior optical mouse is not hidden to anybody. An optical mouse works by having a low resolution camera inside it which takes around 1500 to 6000 pictures per second of the surface beneath it, and by analyzing these images, it calculate the position, speed and movement of the mouse.When a mouse is connected with the computer, a red LED starts glowing. This light is focused on the surface beneath the mouse by a special type of lens (HDNS-2100). The reflected light falls back to the camera integrated in Optical Mouse Sensor. The camera takes images of the surface with a frequency in the range of 1500 to 6000 images per second to calculate the position of mouse.
Operating System : What is an Operating System
During the year 1950, the computer could carry out operation for only a single program at a time. The machine would be loaded with the program and the machine would be operated only after the program was completely loaded. Debugging of a program could be carried out using toggle switches and panel lights on the front panel.An Operating System is software made of data and programs that has a control to execute the application programs. It acts as an interface between hardware and applications. An Operating system serves as an interface between the programmer and computer hardware. Operating systems are present in the electronic devices such as video game console, web servers, supercomputers, cellular phones and many more.
Web Browsers : What is Web Browser
By the time you are reading this article, certainly you are already using a web browser which is presenting this article content in a rich text/graphical format on your computer screen. A web browser or frequently called as browser is an application software that is installed on a computer to provide access to the World Wide Web. I t fetches the web pages from the server along with the necessary files like, images, flashes, videos etc, interprets them and then displays it on the screen. All you have to do is simply type the URL (Uniform Resource Locator) of a webpage in the address bar and the browser will bring the web page on your screen.
Internet : What is Internet
When the computing era took a major leap in the 80s, it was all just about the operating systems and the programming languages. People were getting gaga over the heavy technology revolution thinking that this is the one thing that the world needed to get over the bounds of time and space, and as usual, they were wrong. It was not long after the computer revolution that a tide, a blizzard of communication arrived. This technology now makes the computers look lifeless if they don’t have it. Connecting the corners of the cobwebbed world even from its remotest corner is the ‘Internet’. Not confining itself to any particular definition, the internet can be defined as the wired or wireless mode of communication through which one can receive, transmit information that can be used for single or multiple operations .
Hacking: Understanding Hacking & Types of Hacking
The unceasing quest of human mind has conceived to almost all crucial inventions of the world. Hacking dates back its inception to the same human urge to know and hence explore things. Hacking is a practice of peeping into the extreme technical details of any computer application, program, or the whole system in order to extend its capabilities or alter its functionalities. People who rightly follow this practice of hacking are termed as ‘hackers’. A hacker’s vision towards solving any technical problem is undoubtedly beyond the perception of any normal computer expert. The open-source coding has been very beneficial for hackers to test and invent out of their passion for programming, say UNIX is the best example.