Suppose, one has a home automation system installed which can be accessed from a mobile device. That is a great power as the user can access the electronic appliances and various common household commodities imparted intelligence through embedded electronics from anywhere and anytime. What about the same home automation system is unethically hacked by someone and out turn to be a means for theft in the house. Here the glorious concept of IOT comes with a caution – ‘Security’.
IOT security is a concern that must be taken care beforehand in any IOT application development. The security is not an afterthought. It must be integral within the development of IOT application.
Due to diversity of IOT devices, scale and variety of data and interconnected nature of IOT communication, it is important that appropriate security measures are deployed at every architectural layer of IOT. The security measures need to be applied for both informational as well as communication resources deployed within a system. The security features must be customized according to different use cases of IOT as well.
The security in an IOT system implies that the informational resources in an IOT system are accessed by only authorized users or devices. The authorized user must be able to add, remove or modify informational resources. They must be able to access the resources in their authority at any time and from anywhere. They must have proper backup options not only to secure their authentication but also their data and applications. The security features must be applied at each level – IOT devices, network and the cloud. These security features must be able provide protection in real time as the device to device communication as well as device to cloud communication and even cloud to cloud communication in IOT domain is a real time phenomenon.
From an IOT platform side, providing such security to billions of devices or probably trillions of devices in future is a big challenge. The security at or from even a single device cannot be compromised. The large number of devices connected to a cloud platform also increases the vulnerabilities of the system and let the whole system to be exposed to attackers through any of the device or user. So, the security must be an utmost priority from device level to the cloud platform.
According to ITU-T, the security must be enabled at different layers of the IOT. At the device layer, the IOT device, from powered up to access the data to send the data to cloud, it needs to be high securable. At the device layer, the security can be performed by implementing Authentication, Authorization, Device integrity validation, Access control, Data confidentiality and Integrity protection.
For end to end data delivery, Network layer plays an important role as a mediator. It receives the data from the IOT device and sends the data to the cloud and vice-versa. So the transmitting medium through which the data is sent should be secured enough by implementation of security protocols or security measures within communication protocols at various OSI layers. The network should also perform the security operations like Authorization, Authentication, signaling data confidentiality, Signaling data use and signaling integrity protection while sending and receiving the data.
At the Application layer, when IOT devices send data to the cloud through the network, then the cloud must store the data, does some processes and analytics and based on those analytics, it must take some kind of actions or provide insights. So, at the application layer also, it is important that security measures like Authorization, Authentication, Application data confidentiality and integrity protection, privacy protection, security audit and anti-virus protection are implemented.
So, there are security measure recommendations for each layer of the IOT architecture. The whole application needs to be fully secured at every level from bottom to top then only the IOT application can be reliably and effectively used.
End to End Encryption – Security must be defined throughout the device lifecycle – from the initial design to the operational environment. The security which is enabled on IOT devices, the same security needs to be enabled on the network. In a bottom to top approach (from device powered up to storage of data on the cloud), the security and encryption measures can be represented by the following block diagram –
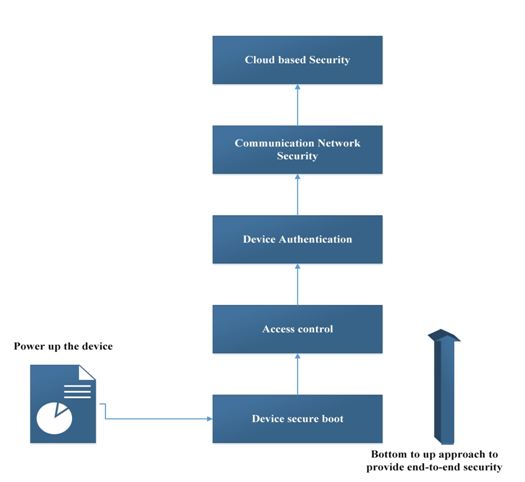
Fig. 1: Block Diagram of IOT Security
1) Device Secure Boot – To run an IOT device securely, the secure booting process must be done in the first place. After accessing the device through secure boot, then only, the data should be sent or shared. This is the first step at device layer to provide the security.
When the device is first powered up, the boot loader which is the main process code of the device needs to be verified (means the boot loader is genuine or not should be checked). Only when it is done, the rest process of the device can be assured.
The boot loader code for the device is developed using a secure development process. When the manufacturer develops a device, it stores a private key with the public key on a secure storage of the device. Now, when the bootloader code is developed for that device, a cryptographic hash of it is digitally signed with the device’s private key. Whenever a bootloader firmware is to be installed on the device, the hash signature is checked against the device’s public key just to confirm that it is an authenticated hash value from the manufacturer. The firmware code is then hashed again. Then the new hashed value is compared with the previous signed hash. If the both signed hash match each other (which indicates the firmware code has not been changed), only then the new firmware is installed.
Thereafter, whenever the device boots, the authenticity and integrity of the installed boot loader code should be verified using cryptographically generated digital signatures. Now the root of trust has been established, but it doesn’t mean that the device is now fully secured. It still needs protection in terms of accessing the data and connection with the network.
2) Access Control – Now, after the device is securely booted, the data in the IOT device needs to be secured. The data should be accessed by the trusted users who have the access to operate the device. For example, an operating system allows access to the file system for only the administrator and not other unauthenticated users. Only root user can access all the data. No other user can access all the resources in the system. For the IOT device, Access control is needed to make sure that only trusted users can access all the information and can control that device. There should be some kind of pass keys or some other security to authenticate the data on device which should be given to only the trusted users so that they can only access the data securely and privately.
3) Device Authentication – After the data is secured at device end, it needs to be secured when the IOT devices try to connect to the network. When it tries to connect to the network, the device should allow some kind of authentication prior to receive or transmit the data over the network. For example, to access a corporate websites, the user needs to get the user authentication by providing user name and password. Many times, the users need to provide multi-factor authentication which may also include biometric authentication through fingerprint or retina scan. In the same way, device or machine authentication should be there to allow device to access a network in a secured way.
4) Network Security – The IOT devices send the data to the cloud in a secure way. Now, there is the responsibility of the network to securely and unchangeably receive and transmit the data to the cloud for further processing. There will be some kind of attacks like Man-in-the-middle attack. So, there should be some kind of authentication, authorization and transportation layer security. Different protocols use different transportation layer security to securely transmit the data from the device to the network. There are also many security protocols to secure the data over the network.
5) Cloud based Security – Now after enabling the security at the network layer, the data is being stored, processed and analyzed for actions or insights on the cloud. So, there comes a call for cloud based security. The cloud on which the data is going to be stored should be secured enough so that Users (other than owner who has the access to control the cloud) can never access the cloud because the main data is stored on cloud and it needs to be fully secured. There are many secured clouds in the market like IBM Bluemix and AWS IOT cloud which provide full control to store and access the data in a secure way.
The IOT is nothing without security. The above mentioned security measures must be enabled as integral part of IOT development. So that, there is no route for the attackers to hack the devices, network or the cloud.
From the next tutorial, practical IOT development with ESP8266 will be started. ESP8266 is a Wi-Fi Microchip with full TCP-IP stack. It comes available in several modules which can be used as development boards for IOT. The boards can be easily connected to a network using various application layer protocols and interfacing through different physical layer technologies.
The next tutorial will be an in-depth discussion on MQTT, an application layer protocol. Then, in the coming tutorials, the ESP-01 module will be connected with the internet using MQTT protocol.
Filed Under: Featured Contributions


Questions related to this article?
👉Ask and discuss on Electro-Tech-Online.com and EDAboard.com forums.
Tell Us What You Think!!
You must be logged in to post a comment.