Communication between two LoRa end-node devices can happen seamlessly. Both end-node devices include the LoRa E5 Mini Board, which switches quickly between sending and receiving messages — making two-way communication possible.
In this setup, communication begins with one device sending a message and waiting for confirmation. Upon receipt, the receiving device sends a reply confirming the message was received. This simple exchange shows how efficient and dependable LoRa technology is for communicating.
Abstract
- Identify the original ST-Link
- Upload the code to the Lora E5 Mini Board
- Learn how to send and receive messages
- Learn how to program the flow or algorithm
Requirements
- Lora E5 Mini Board from Seed Studio
Uploading the code
The code is carefully created so the LoRa E5 Mini efficiently receives data through a universal asynchronous receiver transmitter (UART). Then, it sends this data to another node device.
For simplicity, a project file and a matching hex file are included.
The hex file is made to upload directly to the LoRa E5 Mini Board, making the installation process more efficient. This approach ensures a user-friendly experience while using the full capabilities of the LoRa E5 Mini.
However, the project file requires compilation within the STM32cube IDE before it can be uploaded onto E5 Mini Board.
Here are the steps…
1. Locating a genuine ST-Link V2 is important for the LoRa code, as clone ST-Link variants might not be compatible. This means it’s necessary to recognize the original ST-Link. One reliable method for identification involves examining the hardware components.
Upon close analysis, a genuine ST-Link V2 has an STM chip, indicating authenticity. The clones are typically imported from China and look slightly different.
This project requires a smooth “flashing process,” which occurs reliably with a genuine ST-Link with the STM chip (see image below). Knowing the difference will ensure compatibility and proper programming.
2. Connect five wires to the LoRa E5 Mini Board as indicated in the below image, including 3V3, SWDIO, SWCLK, RST, and GND.
3. Open the STM32CUBE Programmer and click on the ‘Disconnect’ button.
4. Select the Hex File by clicking on the Open File tab.
5. Click on the ‘Download’ button to upload the code.
6. Once a pop-up appears, the download process is complete and has gone correctly.
How to send and receive messages
Connect the device to a computer and open the ‘Serial Terminal.’ The Arduino Serial Terminal is used as a demonstration below.
1. Connect the device to a respective port and open the Serial Terminal, Baud Rate 9600, and select both ‘NL’ and ‘CR’ as shown in the image.
2. Send any message from one serial terminal, and it should appear in the second terminal. If the sender receives the reply, “SENT CONFIRMED!!” the message has been received successfully.
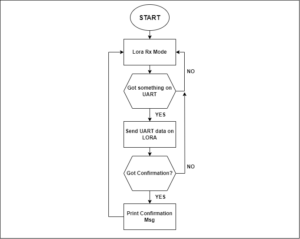
The algorithm
Understanding the code
1. When the code begins, it ‘Starts Listening on UART’ and ‘Starts Receiving’ on Lora.
2. Below is the CMD_GetChar function, which will be called when there’s data on the UART. When this occurs, the UART stores the until ‘\n’ is detected. Then, it sends the stored buffer to the LoRa.
3. If there’s no response from the receiving device, then this function is called…
4. When the device receives data on LoRa, it prints the RSSI and SNR values.
5. When the device receives data over LoRa, it compares the string. If the string is ‘*’ then the message has been confirmed. If there’s any other string meaning, it will print the message on serial and send ‘*’ to another device to confirm that the message has been received.
The messaging device
The above messaging device example can go from a simple idea to a real process with practical improvements. Integrating a screen, keypad, and battery renders it significantly more portable and valuable — allowing for improved user interaction.
Implementing a power-efficient sleep mode can extend the device’s battery life. This would be ideal in remote areas without reliable Internet access. The device can ensure smooth data exchanges.
For stronger security, messages can be turned into secret codes, ensuring private communication. Using an encryption method keeps the data safe and stops unauthorized entry, making the device more secure.
These improvements allow the device to become a reliable tool for connecting in remote places, providing a form of communication that would otherwise be lacking.
You may also like:
Filed Under: Tutorials






















Questions related to this article?
👉Ask and discuss on Electro-Tech-Online.com and EDAboard.com forums.
Tell Us What You Think!!
You must be logged in to post a comment.