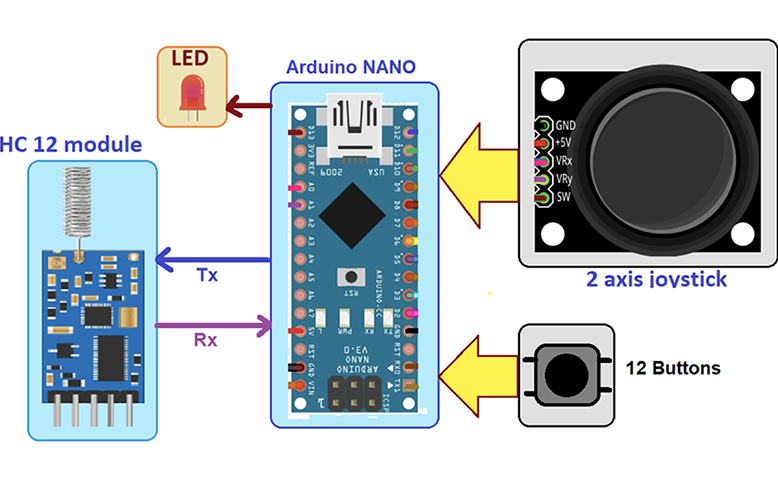
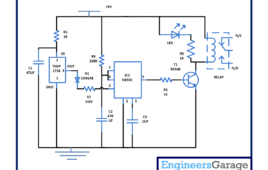
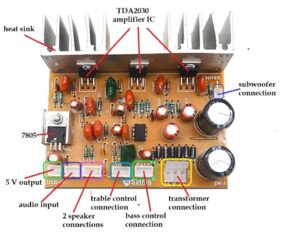
Q-Tech Corporation introduces an advanced oven-controlled crystal oscillator (OCXO) Series for New Space applications. Designed by the company’s German affiliate, AXTAL, the AXIOM75Sx Series features both ultra-low phase noise (close-in and noise floor) and the radiation hardness required for high-performance low-earth orbit (LEO) satellite timing and frequency generation applications. Available for the frequencies of 10MHz (AXIOM75SL)…